Networking Wireshark 3
Ed Smart
CSC 251
Wireshark Lab 3
1. Run nslookup to obtain the IP address of a Web server in Asia. What is the IP address of that server?
Name: http://www.misu.ait.ac.th
Address: 203.159.12.3
Aliases: http://www.asdu.ait.ac.th
The IP address is 2.3.159.12.3.
2. Run nslookup to determine the authoritative DNS servers for a university in Europe.
ox.ac.uk nameserver = dns2.ox.ac.uk
ox.ac.uk nameserver = ns2.ja.net
ox.ac.uk nameserver = dns0.ox.ac.uk
ox.ac.uk nameserver = dns1.ox.ac.uk
The authoritative DNS servers for the University of Oxford are dns2.ox.ac.uk, ns2.ja.net, dns0.ox.ac.uk, and dns1.ox.ac.uk.
3. Run nslookup so that one of the DNS servers obtained in Question 2 is queried for the mail servers for Yahoo! mail. What is its IP address?
Server: dns2.ox.ac.uk
Address: 163.1.2.190
The IP address is 163.1.2.190.
4. Locate the DNS query and response messages. Are they sent over UDP or TCP?
The DNS query and response messages are sent over TCP.
5. What is the destination port for the DNS query message? What is the source port of DNS response message?
Destination port: domain (53) This is the destination port for the DNS query message.
Source port: domain (53) This is the source port of the DNS response message.
6. To what IP address is the DNS query message sent? Use ipconfig to determine the IP address of your local DNS server. Are thesetwo IP addresses the same?
The IP address the DNS query message is sent to is 10.40.4.44. The IP address of my local DNS server is also 10.40.4.44.
7. Examine the DNS query message. What “Type” of DNS query is it? Does the query message contain any “answers”?
http://www.ietf.org: type A, class IN
Answer RRs: 0
The DNS query message of type A and does not contain any answers.
8. Examine the DNS response message. How many “answers” are provided? What do each of these answers contain?
One answer is provided and contains the following information:
http://www.ietf.org: type A, class IN, addr 12.22.58.30
Name: http://www.ietf.org
Type: A (Host address)
Class: IN (0x0001)
Time to live: 30 minutes
Data length: 4
Addr: 12.22.58.30 (12.22.58.30)
9. Consider the subsequent TCP SYN packet sent by your host. Does the destination IP address of the SYN packet correspond to any of the IP addresses provided in the DNS response message?
The destination IP address of the subsequent TCP SYN packet sent by my host does not correspond to any of the IP addresses provided in the DNS response message.
10. This web page contains images. Before retrieving each image, does your host issue new DNS queries?
Yes, my host does issue new DNS queries before retrieving each image.
11. What is the destination port for the DNS query message? What is the source port of DNS response message?
The destination port for the DNS query message is Destination port: domain (53). The source port of the DNS response message is Source port: domain (53).
12. To what IP address is the DNS query message sent? Is this the IP address of your default local DNS server?
The DNS query message is sent to the IP 10.40.4.44, which is the IP address of my default local DNS server.
13. Examine the DNS query message. What “Type” of DNS query is it? Does the message query contain any “answers”?
Type: AAAA (IPv6 address)
Answer RRs: 0
The DNS query is of type AAAA and contains no answers.
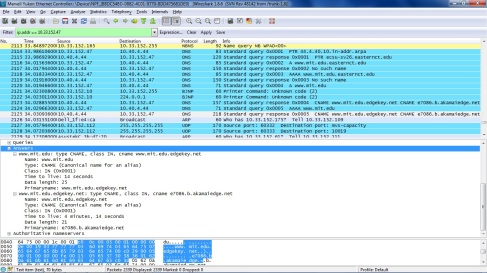
14. Examine the response message. How many “answers” are provided? What do each of these answers contain?
Answer RRs: 2
The first answer contains the following information:
http://www.mit.edu: type CNAME, class IN, cname http://www.mit.edu.edgekey.net
Name: http://www.mit.edu
Type: CNAME (Canonical name for an alias)
Class: IN (0x0001)
Time to live: 14 seconds
Data length: 25
Primaryname: http://www.mit.edu.edgekey.net
The second answer contains the following information:
http://www.mit.edu.edgekey.net: type CNAME, class IN, cname e7086.b.akamaiedge.net
Name: http://www.mit.edu.edgekey.net
Type: CNAME (Canonical name for an alias)
Class: IN (0x0001)
Time to live: 4 minutes, 14 seconds
Data length: 21
Primaryname: e7086.b.akamaiedge.net
15. Provide a screenshot
16. To what IP address is the DNS query message sent? Is this the IP address of your default local DNS server?
The DNS query message is sent to the IP 10.40.4.44, which is the IP of my default local DNS server.
17. Examine the DNS query message. What “Type” of DNS query is it? Does the message query contain any “answers”?
mit.edu: type NS, class IN
Answer RRs: 0
The DNS query message is of type NS and does not contain any answers.
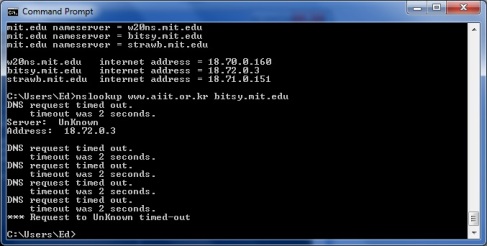
18. Examine the DNS response message. What MIT nameservers does the response message provide? Does this response also provide the IP addresses of the MIT
nameservers?
mit.edu: type NS, class IN, ns w20ns.mit.edu
mit.edu: type NS, class IN, ns bitsy.mit.edu
mit.edu: type NS, class IN, ns strawb.mit.edu
The MIT nameservers the response message provides are w20ns.mit.edu, bitsy.mit.edu, and strawb.mit.edu.
w20ns.mit.edu: type A, class IN, addr 18.70.0.160
bitsy.mit.edu: type A, class IN, addr 18.72.0.3
strawb.mit.edu: type A, class IN, addr 18.71.0.151
The IP address of w20ns.mit.edu is 18.70.0.160
The IP address of bitsy.mit.edu is 18.72.0.3
The IP address of strawb.mit.edu is 18.71.0.151
19. Provide a screenshot.
Now repeat the previous experiment, but instead issue the command:
nslookup http://www.aiit.or.kr bitsy.mit.edu
I could not complete the last part of the assignment due to the destination of the given query being unreachable.
Networking Wireshark 2
Ed Smart
CSC 251
Wireshark Lab 2
1. Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running?
Both my browser and the server are running HTTP version 1.1
My browser:
104
7.557207000
10.33.152.47
209.190.113.66
HTTP
690
GET/related?s=850&md=21&pid=13a0656f8a08dbdcec1d20ff54578935&sess=iqtSGw66HA&q=http%3A//gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file1.html&sub=16912&prev=http%3A//wps.pearsoned.com/wps/media/objects/13865/14198700/wiresharkLabs/Wireshark_HTTP_v6.1.pdf HTTP/1.1 <- Version is stated here
Server:
119
7.616230000
209.190.113.66
10.33.152.47
HTTP
487
HTTP/1.1 200 OK (application/json) <- Version is stated in this line
2. What languages (if any) does your browser indicate that it can accept to the server?
My browser indicates that it can accept English
Accept-Language: en-US,en;q=0.5\r\n
3. What is the IP address of your computer? Of the gaia.cs.umass.edu server?
The IP address of my computer is 10.33.152.47. The IP address of the gaia.cs.umass.edu server is 209.190.113.66.
HTTP GET message:
104 7.557207000 10.33.152.47 (source) 209.190.113.66 (destination) HTTP 690
4. What is the status code returned from the server to your browser?
The status code returned from the server to my browser was 200.
HTTP/1.1 200 OK\r\n
Status Code: 200
5. When was the HTML file that you are retrieving last modified at the server?
Date: Sun, 28 Apr 2013 07:55:12 GMT\r\n
6. How many bytes of content are being returned to your browser?
117 bytes of content are being returned.
Content-Length: 117\r\n
7. By inspecting the raw data in the packet content window, do you see any headers within the data that are not displayed in the packet-listing window? If so, name one.
There are no headers within the data that are not displayed in the
8. Inspect the contents of the first HTTP GET request from your browser to the server. Do you see an “IF-MODIFIED-SINCE” line in the HTTP GET?
There is no “IF-MODIFIED-SINCE” line in the first HTTP GET request.
9. Inspect the contents of the server response. Did the server explicitly return the contents of the file? How can you tell?
The server explicitly returned the contents of the file.
10. Now inspect the contents of the second HTTP GET request from your browser to the server. Do you see an “IF-MODIFIED-SINCE:” line in the HTTP GET request? If so, what information follows the “IF-MODIFIED-SINCE:” header?
If-Modified-Since: Sun, 28 Apr 2013 18:37:01 GMT\r\n
11. What is the HTTP status code and phrase returned from the server in response to this second HTTP GET? Did the server explicitly return the contents of the file? Explain.
Status Code: 304
Response Phrase: Not Modified
The server did not return the text of the file because the file has not been modified.
12. How many HTTP GET requests did your browser send? Which packet number in the trace contains the GET message for the Bill of Rights?
My browser sent one HTTP GET request, and the packet number in the trace that contains the GET message for the Bill of Rights is 59.
Line-based text data: text/html
<html><head> \n
<title>Historical Documents:THE BILL OF RIGHTS</title></head>\n
13. Which packet number in the trace contains the status code and phrase associated with the response to the HTTP GET message?
The packet number in the trace that contains the status code and phrase associated with the response to the HTTP GET message is also 59.
14. What is the status code and phrase in the response?
Status Code: 200
Response Phrase: OK
15. How many data-containing TCP segments were needed to carry the single HTTP response and the text of the Bill of Rights?
One was needed to carry the HTTP response and the Bill of Rights text.
59 6.171688000 128.119.245.12 10.33.152.47 HTTP 501 HTTP/1.1 200 OK (text/html)
Content-Length: 4500\r\n
Line-based text data: text/html
<html><head> \n
<title>Historical Documents:THE BILL OF RIGHTS</title></head>\n
…
<p>The Conventions of a number of the States having, at the time of adopting\n
the Constitution, expressed a desire, in order to prevent misconstruction\n
…
<p>The powers not delegated to the United States by the Constitution, nor prohibited \n
by it to the states, are reserved to the states respectively, or to the people.</p>\n
</body></html>
16. How many HTTP GET request messages did your browser send? To which internet address were these GET request messages sent?
My browser sent three HTTP GET request messages; one to the address 128.119.245.12, one to 165.193.140.14, and one to 128.119.240.90.
51 4.779459000 10.33.152.47 128.119.245.12 HTTP 393 GET /wireshark-labs/HTTP-wireshark-file4.html HTTP/1.1
76 6.660074000 10.33.152.47 165.193.140.14 HTTP 606 GET /assets/hip/us/hip_us_pearsonhighered/images/pearson_logo.gif HTTP/1.1
77 6.664044000 10.33.152.47 128.119.240.90 HTTP 424 GET /~kurose/cover_5th_ed.jpg HTTP/1.1
17. Can you tell whether your browser downloaded the two images serially, or whether they were downloaded from the two websites in parallel? Explain.
The images were downloaded from the websites in parallel. The request for the second image file was made before the first image file was received.
55 4.801456000 128.119.245.12 10.33.152.47 HTTP 1071 HTTP/1.1 200 OK (text/html)
100 6.696267000 165.193.140.14 10.33.152.47 HTTP 1136 HTTP/1.1 200 OK (GIF89a)
224 6.781848000 128.119.240.90 10.33.152.47 HTTP 534 HTTP/1.1 200 OK (JPEG JFIF image)
18. What is the server’s response (status code and phrase) in response to the initial HTTP GET message from your browser?
Status Code: 401
Response Phrase: Authorization Required
19. When your browser sends the HTTP GET message for the second time, what new field is included in the HTTP GET message?
Authorization: Basic c21hcnRlZDpXaGF0aXN0aGlzMQ==\r\n
Networking Wireshark 1
Ed Smart
CSC 251
Wireshark Lab 1
1. List 3 different protocols that appear in the protocol column in the unfiltered packet-listing window in step 7 above.
Three different protocols that appear are HTTP, TLSv1, and TCP.
2. How long did it take from when the HTTP GET message was sent until the HTTP OK reply was received?
It took .0613 seconds from when the HTTP GET message was sent until the HTTP OK reply was received.
3. What is the Internet address of the gaia.cs.umass.edu (also known as www-net.cs.umass.edu)? What is the Internet address of your computer?
The internet address of gaia.cs.umass.edu is 209.190.113.66. The internet address of my computer is 10.33.152.47.
4. Print the two HTTP messages (GET and OK) referred to in question 2 above.
HTTP GET message:
257
24.485585000
10.33.152.47
209.190.113.66
HTTP
617
GET/related?s=850&md=21&pid=13a0656f8a08dbdcec1d20ff54578935&sess=iqtSGw66HA&q=http%3A//gaia.cs.umass.edu/wireshark-labs/INTRO-wireshark-file1.html&sub=16912&prev=http%3A//www.yahoo.com/ HTTP/1.1
HTTP OK message:
307
24.546928000
209.190.113.66
10.33.152.47
HTTP
487
HTTP/1.1 200 OK (application/json)
Networking Homework 5
Ed Smart
CSC 251
Homework 5
P6. In the text we have used the term connection-oriented service to describe a transport-layer service and connection service for a network-layer service. Why the subtle shades in terminology?
The subtle shades in terminology are due to the facts that in a transport-layer service where the network layer has no connection, the end systems involved maintain the connection without action from the routers, while a network-layer service requires a set of routers to maintain a connection between end systems. This is why a transport-layer service is said to be a connection-oriented service and a network-layer service is a connection service.
P11. Consider a datagram network using 8-bit host addresses. Suppose a router uses longest prefix matching and has the following forwarding table:
Prefix Match Interface
00 0
010 1
011 2
10 2
11 3
For each of the four interfaces, give the associated range of destination host addresses and the number of addresses in the range.
Prefix Match Range Minimum Maximum
00 2^6 00000000 = 0 00111111 = 63
01 2^6 01000000 = 64 01111111 = 127
10 2^6 10000000 = 128 10111111 = 191
11 2^6 11000000 = 192 11111111 = 255
P17. Consider the topology shown in Figure 4.17. Denote the three subnets with hosts (starting clockwise at 12:00) as Networks A, B, and C. Denote the subnets without hosts as Networks D, E, and F.
a. Assign network addresses to each of these six subnets, with the following constraints: All addresses must be allocated from 214.97.254/23; Subnet A should have enough addresses to support 250 interfaces; Subnet B should have enough addresses to support 120 interfaces; and Subnet C should have enough addresses to support 120 interfaces. Of course, subnets D, E and F should each be able to support two interfaces. For each subnet, the assignment should take the form a.b.c.d/x or a.b.c.d/x – e.f.g.h/y.
Subnet A: 214.97.255 / 24
256 addresses
Subnet B: 214.97.254.0 / 25 – 214.97.254.0 / 29
120 addresses
Subnet C: 214.97.254.128 / 25
128 addresses
Subnet D: 214.97.254.0 / 31
2 addresses
Subnet E: 214.97.254.2 / 31
2 addresses
Subnet F: 214.97.254.4 / 30
4 addresses
b. Using your answer to part (a), provide the forwarding tables (using longest prefix matching) for each of the three routers.
Router 1
Prefix Interface
11010110 01100001 11111111 0
11010110 01100001 11111110 0000000 3
11010110 01100001 11111110 000001 5
Router 2
Prefix Interface
11010110 01100001 11111111 000001 5
11010110 01100001 11111110 0000001 4
11010110 01100001 11111110 1 2
Router 3
Prefix Interface
11010110 01100001 11111111 0000000 3
11010110 01100001 11111110 0 1
11010110 01100001 11111110 0000001 4
P37. Consider the network shown below. Suppose AS3 and AS2 are running OSPF for their intra-AS routing protocol. Suppose AS1 and AS4 are running RIP for their intra-AS routing protocol. Suppose eBGP and iBGP are used for the inter-AS routing protocol. Initially suppose there is no physical link between AS2 and AS4.
a. Router 3c learns about prefix x from which routing protocol: OSPF, RIP,
eBGP, or iBGP?
eBGP
b. Router 3a learns about x from which routing protocol?
iBGP
c. Router 1c learns about x from which routing protocol?
eBGP
d. Router 1d learns about x from which routing protocol?
iBGP
Programming Languages Homework 7
Ed Smart
CSC 340
Homework 7
6.5 (a) Describe the strings that are represented by the regular expression:
[0-9]+((E|e)(\+|\-)?[0-9]+)?
[0-9]: This indicates a set of items.
+: This means “one or more than one.”
|: When placed between two items, this means “or.”
\: “Escape”
?: The item before this symbol is optional.
(E|e): “E or e”
(\+|\-): Optional “+ or -”
((E|e)(\+|\-)?[0-9]+)?: The “?” after this string means the string is optional.
(b) Write a regular expression for C identifiers consisting of letters, digits, and the underscore character ‘_’, and starting with a letter or underscore.
[A-Z|a-z|_]+([A-Z|a-z|0-9|_])?
6.13 Unary minuses can be added in several ways to the arithmetic expression grammar of Figure 6.17 or Figure 6.18. Revise the BNF and EBNF for each of the cases that follow so that it satisfies the stated rule:
(a) At most, one unary minus is allowed in each expression, and it must come at the beginning of an expression, so -2 + 3 is legal (and equals 1) and -2 + (-3) is legal, but -2 + -3 is not.
BNF revision:
uminus -> – expr | term
expr -> expr + term | term
term -> term * factor | factor
factor -> (expr) | number
number -> number digit | digit
digit -> 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9
EBNF revision:
uminus -> – expr | term
expr -> term {+ term}
term -> factor {* factor}
factor -> (expr) | number
number -> digit {digit}
digit -> 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9
(b) At most, one unary minus is allowed before a number or left parenthesis, so -2 + -3 and -2 * -3 are legal, but –2 and -2 + –3 are not.
BNF revision:
uminus -> – expr | term
expr -> expr + term | term
term -> term * factor | factor
factor -> (expr) | number
number -> number digit | digit
digit -> 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9
EBNF revision:
expr -> term {+ term}
term -> factor {* factor}
uminus -> (-expr) | number
factor -> (expr) | number
number -> digit {digit}
digit -> 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9
(c) Arbitrarily many unary minuses are allowed before numbers and left parentheses, so everything above is legal.
BNF revision:
uminus -> (-expr) | number
expr -> expr + term | term
term -> term * factor | factor
factor -> (expr) | number
number -> number digit | digit
digit -> 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9
EBNF revision:
uminus -> (-expr) | number
expr -> term {+ term}
term -> factor {* factor}
factor -> (expr) | number
number -> digit {digit}
digit -> 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9
6.15 Finish writing the pseudocode for a recursive-descent recognizer for the English grammar of Section 6.2 that was begun in Section 6.6.
void sentence() {
nounPhrase();
verbPhrase();
}
void nounPhrase() {
article();
noun();
}
void verbPhrase() {
article();
verb();
}
void article() {
if (token == “a”) match (“a”, “a expected”);
else if (token == “the”) match (“the”, “the expected”);
else error (“article expected”);
}
void noun() {
if (token == “spoon”) match (“spoon”, “spoon expected”);
else if (token == “fork”) match (“fork”, “fork expected”);
else error (“noun expected”);
}
void verb() {
if (token == “stop”) match (“stop”, “stop expected”);
else if (token == “go”) match (“go”, “go expected”);
else error (“verb expected”);
}
Networking Homework 4
Ed Smart
CSC 251
Homework 4
P5. Suppose that the UDP receiver computes the Internet checksum for the received UDP segment and finds that it matches the value carried in the checksum field. Can the receiver be absolutely certain that no bit errors have occurred? Explain.
The receiver cannot be absolutely certain that no bit errors have occurred, due to the fact that the sum of the bits in a packet will remain the same if those bits are 0 and 1 or 1 and 0. Thus, even if an error did occur, this process would execute.
P10. Consider a channel that can lose packets but has a maximum delay that is known. Modify protocol rdt2.1 to include sender timeout and retransmit. Informally argue why your protocol can communicate correctly over this channel.
P15. Consider the cross-country example shown in Figure 3.17. How big would the window size have to be for the channel utilization to be greater than 98 percent? Suppose that the size of a packet is 1,500 bytes, including both header fields and data.
(1500 bytes * 8) / 10^9 = 0.00001.2 seconds = 0.012 milliseconds
utilization = 0.98
(0.012x) / 30.012 = 0.98
0.012x = 29.41176
x = 2450.98
The window size would have to be approximately 2451 packets.
P26. P26. Consider transferring an enormous file of L bytes from Host A to Host B.
Assume an MSS of 536 bytes.
a. What is the maximum value of L such that TCP sequence numbers are not exhausted? Recall that the TCP sequence number field has 4 bytes.
4 bytes = 32 bits
Maximum value of L = 2^32 bits
b. For the L you obtain in (a), find how long it takes to transmit the file. Assume that a total of 66 bytes of transport, network, and data-link header are added to each segment before the resulting packet is sent out over a 155 Mbps link. Ignore flow control and congestion control so A can pump out the segments back to back and continuously.
536 bytes
66 bytes for transport, network, and data-link header
155 Mbps link
536 – 66 = 470 bytes remaining for data
2^32 / 470 = 9,138,228.289 packets needed
9,138,228.289 * 536 = 4,898,090,363 bits = 4899 mb
4899 / 155 = 31.606 seconds
P28. Host A and B are directly connected with a 100 Mbps link. There is one TCP connection between the two hosts, and Host A is sending to Host B an enormous file over this connection. Host A can send its application data into its TCP socket at a rate as high as 120 Mbps but Host B can read out of its TCP receive buffer at a maximum rate of 50 Mbps. Describe the effect of TCP flow control.
The receive buffer will begin to fill up, due to the fact that Host A will be sending data into it faster than Host B can remove the data from it. Once the buffer has completely filled, Host B will send a message to Host A to stop sending data until Host B can remove data from the buffer. Host B will then send a TCP segment to Host A, informing it to continue sending data. The buffer will fill up again and this process will repeat until all of the data has been sent from Host A to Host B.
Programming Languages Homework 6
Ed Smart
CSC 340
Homework 5
5.4 Implement a LinkedPriorityQueue class in Smalltalk. The objects added to this type of queue must recognize the <, =, and > operators. The objects are ranked in the queue from small-est (at the front) to largest (at the rear). If two objects are equal, they are inserted in standard FIFO queue order. Your implementation should make maximum use of the LinkedQueue class developed in Section 5.2.
5.7 In the design of collection classes, some collections are subclasses of other collections (the “is-a” relation), whereas other collections contain or use other collections in their implementations (the “has-a” relation). Pick an example of each type of design and explain why the design decision is preferable to the alternative.
5.8 In Smalltalk, the Dictionary class is a subclass of the Set class, whereas in Java, the Map classes are not included in the Collection class hierarchy as subclasses. Compare and contrast the costs and benefits of these two design decisions.
The Dictionary class in Smalltalk allows a user to find and return a value by using a call function, making it more efficient than the Map classes in Java in that respect. However, anything done to cause a change in the parent class in Smalltalk will also force changes in the subclasses of that class, an outcome that may not be wanted. In Java, each class implements the Map classes individually and in a way independent from each other. Due to this, Java’s design avoids the cost of Smalltalk’s design.
5.22 Study the Comparable interface in Sun’s Java documentation, and modify the Complex class developed in Section 5.3 so that it implements this interface. Explain why this move will enable a programmer to sort arrays or lists of Complex numbers using methods in Java’s Arrays or Collections classes.
5.24 The class diagrams of Figures 5.6 and 5.7 show Java’s List interface and its implementing classes. In Section 5.3, we developed a LinkedStack class as a subclass of AbstractCollection. An alternative implementation, called ArrayStack, includes the
same methods as LinkedStack. Draw a class diagram that places these two classes and a new interface called TrueStack in the appropriate places in the hierarchy. (Hints: The TrueStack interface should extend the Collection interface. The stack classes should extend the AbstractCollection class and also implement the TrueStack interface.)
5.30 Describe the two meanings of the keyword virtual in C++ discussed in the text.
The keyword virtual in C++ is used to define functions as candidates for dynamic binding. The word virtual can also refer to a pure virtual declaration, which is used in order to achieve an abstract function within an abstract class. This is done by using a 0 in the declaration to indicate that the function is null at a particular point. Due to this, the function can’t be call and thus, is an abstract function, rendering its class abstract as well.
5.34 Given the following code in Java:
class A{
public void p(){
System.out.println(“A.p”);
}
public void q(){
System.out.println(“A.q”);
}
public void r(){
p();
q();
}
}
class B extends A{
public void p(){
System.out.println(“B.p”);
}
}
class C extends B{
public void q(){
System.out.println(“C.q”);
}
public void r(){
q();
p();
}
}
…
A a = new B();
a.r();
a = new C();
a.r();
What does this code print? Why?
This code prints the following:
B.p
A.q
C.q
B.p
The code begins by creating an object a of class B. Due to this, p() is called from class B in place of class A, and q() is then called from class A. q() is then called from class C by r() and since class C extends class B, p() is then called from class B.
5.35 Given the following code in C++:
class A{
public:
virtual void p(){
cout << “A.p” << endl;
}
void q(){
cout << “A.q” << endl ;
}
virtual void r(){
p();
q();
}
};
class B : public A{
public:
void p(){
cout << “B.p” << endl;
}
};
class C : public B{
public:
void q(){
cout << “C.q” << endl;
}
void r(){
q();
p();
}
};
…
A a;
C c;
a = c;
a.r();
A* ap = new B;
ap->r();
ap = new C;
ap->r();
What does this code print? Why?